Updating Configurations and Managing Certificates at Scale with NGINX Instance Manager
We launched NGINX Instance Manager earlier this year to help enterprises discover, track, secure, and configure NGINX Open Source and NGINX Plus instances. We are excited to announce NGINX Instance Manager version 1.0 which introduces the following capabilities:
- Tagging of NGINX instances and user roles – Group together assets for simplified management at scale. With just a few clicks you can apply configuration and role-based access control (RBAC) settings to all NGINX instances in a group at once.
- Certificate management – Detect expiring certificates and replace them to ensure secure and uninterrupted services.
Tagging for Simplified Management at Scale
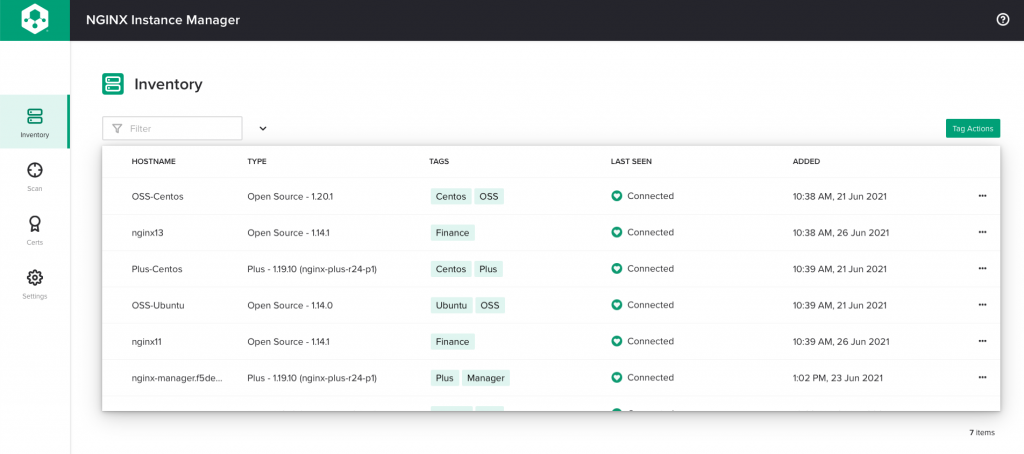
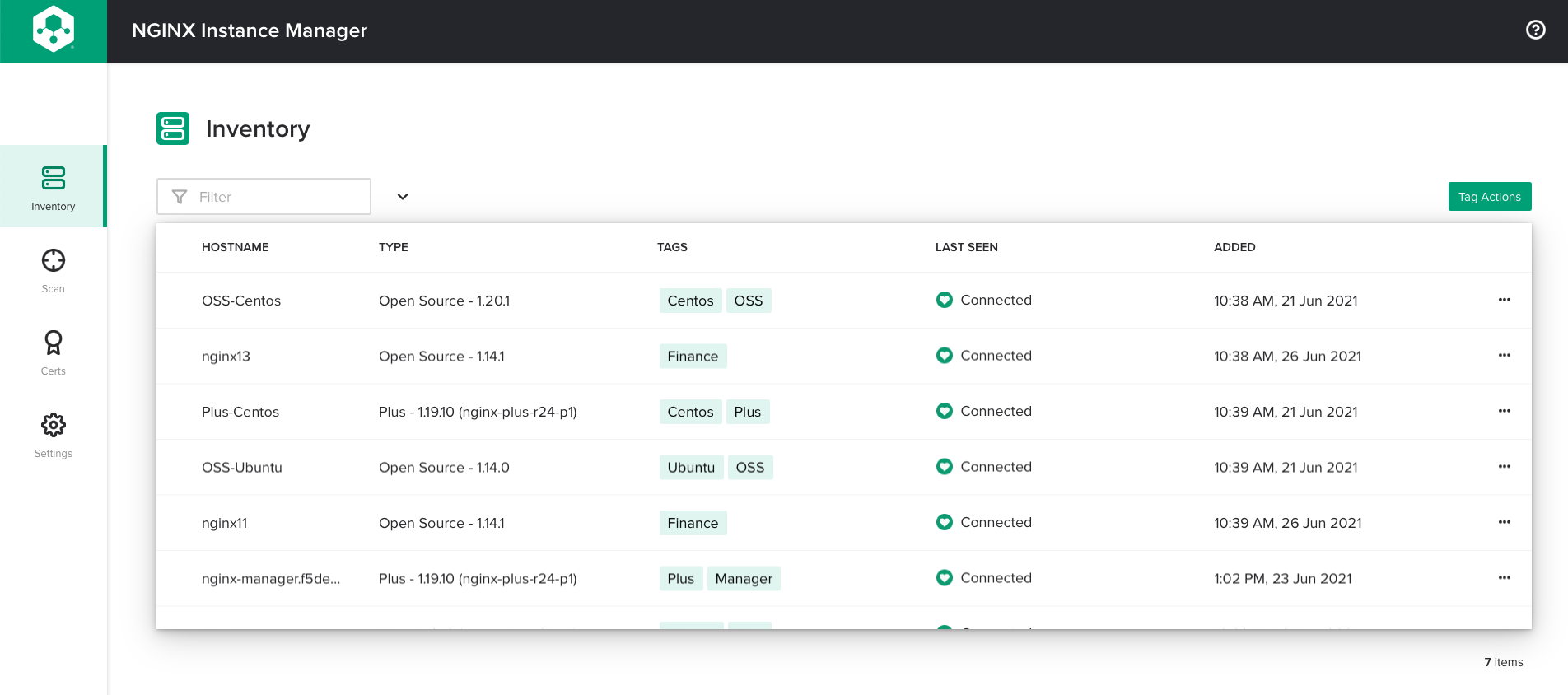
The more NGINX instances you have, the more challenging it can be to manage them. You can now apply tags to NGINX instances and RBAC roles, enabling you to act on all members of a group at once. You can group together NGINX instances or roles based on any characteristic, for example categorizing instances by management team (DevOps, NetOps), purpose (test, sandbox, production), operating system (CentOS, Ubuntu), NGINX model (NGINX Open Source, NGINX Plus), and environment (AWS, on‑premises, private cloud).
With tagging, you can perform tasks like the following faster and easier:
-
Configuration management at scale – You can apply a configuration to all tagged NGINX instances in a group at once, ensuring consistency. In the following screenshot, instances are tagged by operating system and NGINX model.
-
Monitoring in context – Grafana dashboards include a tags field with comma‑separated values. You can construct PromQL queries to present metrics grouped by tag.
-
Access control – With the NGINX Plus implementation of authorization using OpenID Connect and JWTs, you can restrict user access based on tagged roles. For example, you can permit members of the QA team to manage only NGINX instances tagged with test.
Note: This feature is provided as a technology preview. We do not recommend using it in production environments and can provide support on a best‑effort basis only.
In the screenshot, users with the Finance role are granted read‑write access to NGINX instances tagged with Finance, and no other instances. Similarly, users with the Finance_RO role have read‑only access to Finance‑tagged instances only.
In this screenshot, user1 is assigned the Finance role (identified by its Display Name, Finance Read Write).
Certificate Management for Uninterrupted Service
NGINX is now the #1 web server on the Internet. With so many sites relying on it, there’s a potential for outages caused by expired SSL/TLS certificates on NGINX instances. The NGINX Instance Manager certificate management interface enables you to detect expiring certificates and replace them to ensure secure and uninterrupted services.
The report from a certificate scan specifies the number of days remaining before expiration. You can utilize the API to query and keep track of web servers that need a renewed certificate – no separate agent is needed. Once you have identified that a certificate has expired, you can replace it. In fact, you can leverage Instance Manager to update and replace any file referenced in NGINX configuration, including key files and JavaScript files as well as certificates.
The screenshot shows the results of a certificate scan of NGINX instances with IP addresses in the 10.1.1.0/24 range that are listening on port 443.
In this screenshot, the configuration editor is used to upload a certificate to a managed NGINX instance.
Want to Give NGINX Instance Manager a Try?
Download a 30-day free trial or contact us to discuss your use cases.
The post Updating Configurations and Managing Certificates at Scale with NGINX Instance Manager appeared first on NGINX.
Source: Updating Configurations and Managing Certificates at Scale with NGINX Instance Manager