Securing the Perimeter: Achieving Zero Trust with NGINX Plus and SSO/Rest
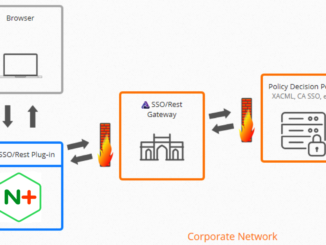
Securing the Perimeter: Achieving Zero Trust with NGINX Plus and SSO/Rest The move to cloud computing means that more of our data, our operations, and our business are being repositioned to face the public Internet; sensitive assets are no longer necessarily tucked away in the corporate data center, accessible only to on‑site personnel. The new risks resulting from this paradigm shift are increasingly rendering existing access control models insufficient and are rapidly driving the security community to embrace the “Zero Trust” approach to security as the gold standard for resource protection. In a Zero Trust architecture, there is no longer a trusted network inside a corporate perimeter and an untrusted world outside. Instead, “microperimeters” are constructed around data and resources, allowing fine‑grained access control policies to be enforced at all locations. (For a detailed discussion of Zero Trust, see the [ more… ]