GPU 딥러닝 모델 학습에 있어서 Amazon EC2 스팟 인스턴스의 활용법
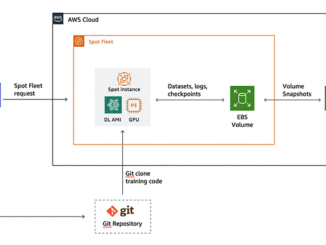
GPU 딥러닝 모델 학습에 있어서 Amazon EC2 스팟 인스턴스의 활용법 여러분이 데이터 세트를 수집하고, 심층 신경망 아키텍처를 설계하고, 학습 루틴 코드를 작성을 완료 하셨다면 지금부터는 강력한 GPU 인스턴스를 사용해 여러 epoch에 걸쳐 대규모 데이터 세트를 이용한 학습을 실행할 차례입니다. 여러분은 이미 NVIDIA Tesla V100 GPU에 기반한 Amazon EC2 P3 인스턴스가 컴퓨팅 집약적인 딥러닝 학습 작업에 적합하다는 사실을 알고 있지만 예산이 빠듯한 관계로 가능한한 학습 비용은 낮추고 싶습니다. 몇 시간 또는 며칠에 걸쳐 학습 작업을 실행하는 딥러닝 연구자 및 개발자라면, 스팟 인스턴스 요금을 통해 훨씬 경제적인 비용으로 고성능 CPU를 이용할 수 있습니다. 스팟 인스턴스를 사용하면 온디맨드 요금에 비해 대폭 할인된 가격으로 여분의 Amazon EC2 컴퓨팅 용량에 액세스할 수 있습니다. 인스턴스 및 리전별 최근 요금 목록을 보려면 스팟 인스턴스 어드바이저를 방문하십시오. 스팟 인스턴스와 온디맨드 인스턴스 사이의 주요 차이점을 알아보려면 이 Amazon EC2 사용 설명서를 검토해 보시기 바랍니다. 스팟 인스턴스는 딥러닝 워크플로우에 적합하지만, 온디맨드 [ more… ]


