NGINX Tutorial: Protect Kubernetes Apps from SQL Injection
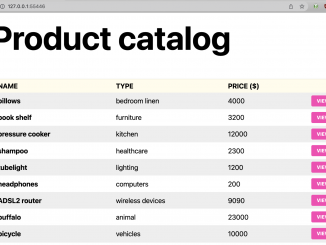
NGINX Tutorial: Protect Kubernetes Apps from SQL Injection Note: This tutorial is part of Microservices March 2022: Kubernetes Networking. Reduce Kubernetes Latency with Autoscaling Protect Kubernetes APIs with Rate Limiting Protect Kubernetes Apps from SQL Injection (this post) Improve Uptime and Resilience with a Canary Deployment (coming soon) You work in IT for a popular local store that sells a variety of goods, from pillows to bicycles. They’re about to launch their first online store, but before launch they’ve asked a security expert to pen test the site before it goes public. Unfortunately, the security expert found a problem! The online store is vulnerable to SQL injection. The security expert was able to exploit the site to obtain sensitive information from your database, including usernames and passwords. Your team has come to you – the Kubernetes engineer – to save the day. [ more… ]


