
Accelerating DDoS Mitigation with eBPF in F5 NGINX App Protect DoS

The battle against DDoS attacks continues to transform. In the 2023 DDoS Attack Trends report, F5 Labs analyzed three years of recent data about distributed denial-of-service (DDoS) attacks and found that while attackers still use complex multi‑vector DDoS attacks, they have also shifted to launching more purely application‑layer (Layer 7) attacks. In 2022 alone, the prevalence of Layer 7 attacks grew by 165%.
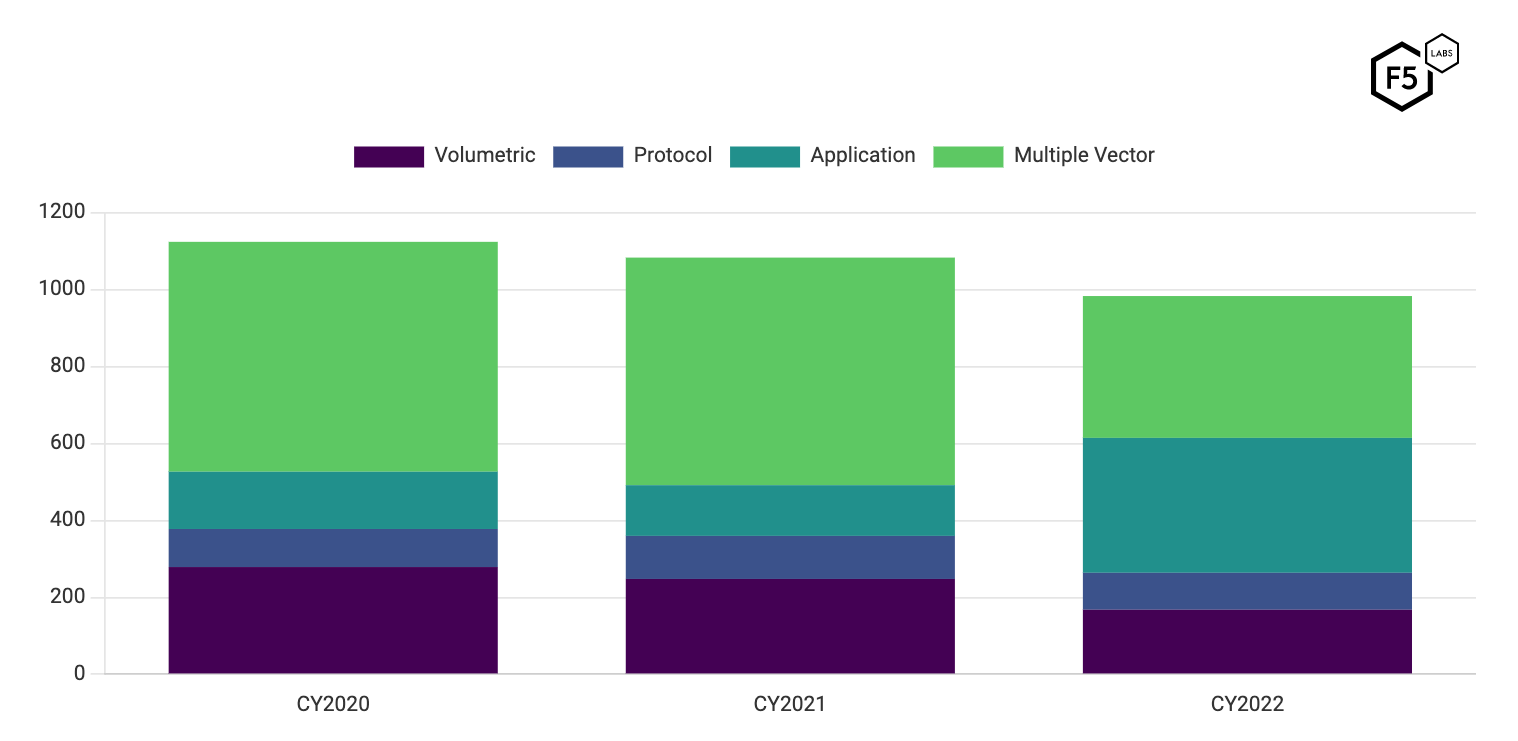
Typically, attackers pursue the easiest path to achieve their goal, whether that means preventing operations of a website or extortion of a target. This rise in Layer 7 attacks may be an indication that it is becoming harder to launch a DDoS attack solely by using a volumetric or protocol strategy, and that application‑layer attacks are proving to be more effective.
Protecting Modern Apps with eBF and XDP
When defending your applications against DDoS attacks, it’s important to take advantage of advances in technology wherever possible to maximize the chance of keeping your applications available (and your users happy). While the extended Berkeley Packet Filter (eBPF) with eXpress Data Path (XDP) technology has been around since 2014, its popularity is currently surging among developer, SRE, and operations communities due to the rising adoption of microservices and cloud‑native architectures.
eBPF
eBPF is a data link layer virtual machine (VM) in the Linux kernel that allows users to run programs safely and efficiently. It also extends the capabilities of the kernel at runtime, without changing the kernel source code nor adding additional kernel modules. eBPF is event‑triggered – it detects specific activity on a Linux host and takes specific action. This technology provides full stack visibility into apps and app services with the ability to trace connectivity and transactions between microservices and end users. The range of available data is quite extensive. It has the ability to address acute observability, analyze network traffic management and runtime security needs, and use its fundamental efficient design to lower compute costs.
Check out the video What is eBPF? from F5 DevCentral for a quick overview of eBPF technology.
XDP
XDP offers the benefit of high‑performance networking. It enables user space programs to directly read and write to network packet data and make decisions on how to handle a packet prior to reaching the kernel level. This technology allows developers to attach an eBPF program to a low‑level hook, implemented by the network device driver within the Linux kernel.
How Does NGINX App Protect DoS Use eBPF?
NGINX App Protect DoS is an advanced behavior‑based Layer 7 DDoS mitigation solution that runs on NGINX Plus and NGINX Ingress Controller to defend HTTP and HTTP/2 apps against attacks like Slowloris and HTTP Flood. In short, NGINX App Protect DoS protects against application‑layer attacks that simple network DDoS solutions cannot detect.
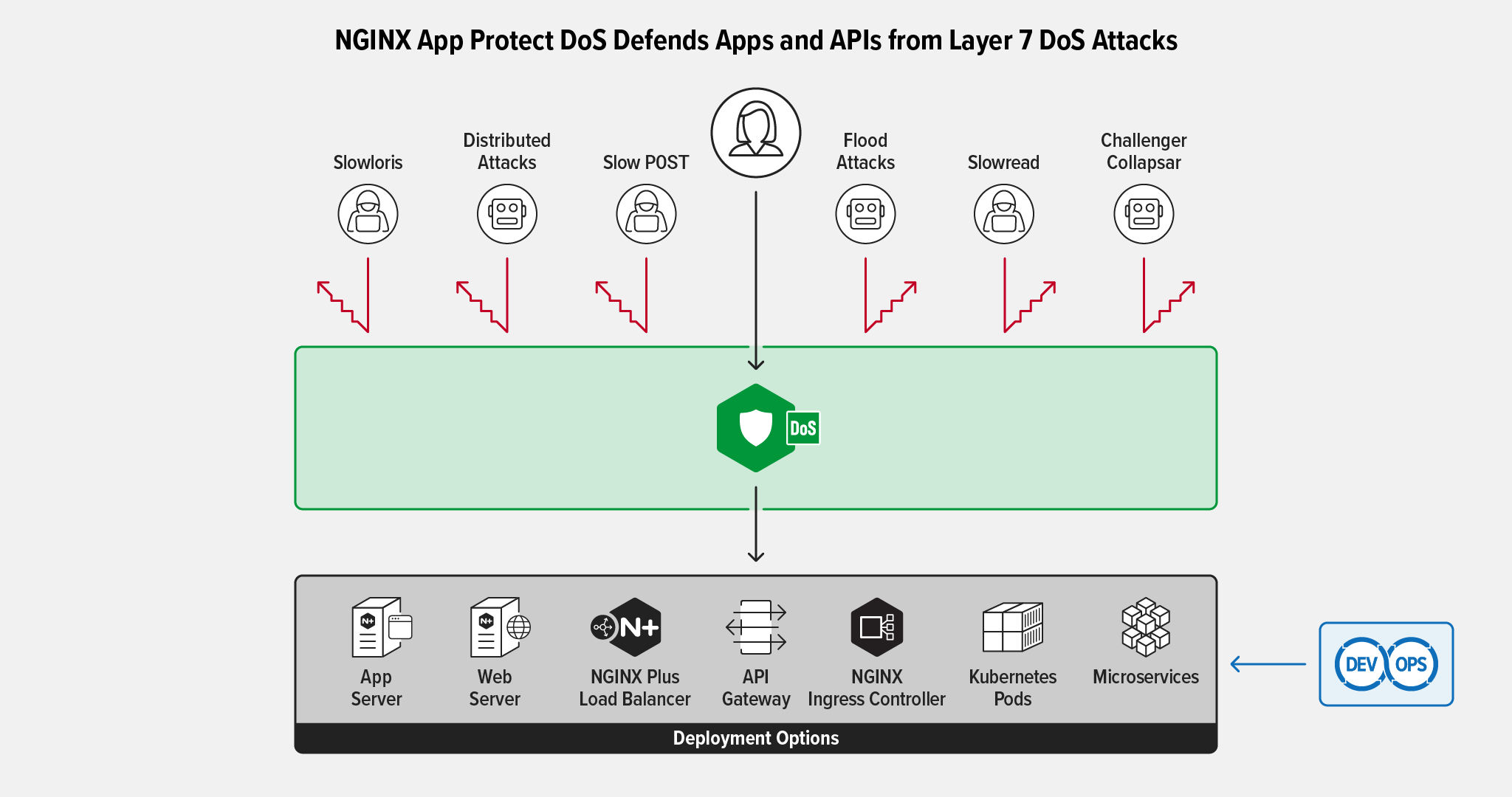
When used with NGINX App Protect DoS, eBPF offers the promise of significantly enhanced DDoS attack absorption capacity. NGINX App Protect DoS uses eBPF (which is not available in NGINX Ingress Controller itself) as part of a multi‑layered solution that accelerates mitigation performance by blocking traffic from bad actors, which are identified by source IP address, alone or in combination with TLS fingerprinting.
Next, let’s look at the basic mechanics of how NGINX App Protect DoS works across three phases: anomaly detection, dynamic rule creation and adaptive learning, and rule enforcement.
Anomaly Detection
NGINX App Protect DoS continuously monitors your protected application and uses machine learning to build a statistical site model of application and client behavior. It observes traffic in real time and tracks over 300 HTTP request metrics to create a constantly updated, comprehensive baseline of activity and performance. In addition to passively monitoring application traffic, NGINX App Protect DoS also performs active application health checks and monitors metrics like response times and dropped requests.
When the application comes under a Layer 7 DDoS attack, the application response times (or error rates) deviate from the learned model and the application protection system is triggered.
Dynamic Rule Creation and Adaptive Learning
After an anomaly is detected, NGINX App Protect DoS dynamically creates rules to identify and block malicious traffic. With the aim of enabling legitimate users to access the application while blocking malicious attackers, it creates a statistical picture of client behavior to identify which users are or are not contributing to the attack.
In addition to deploying dynamic signatures to block attacks, NGINX App Protect DoS continuously measures mitigation effectiveness and applies adaptive learning to constantly provide robust app security and block zero‑day attacks. Once the clients and requests causing an attack are identified, it builds a rule to deny that traffic.
NGINX App Protect DoS implements a multi‑layered defense strategy that includes:
- Blocking bad actors based on IP address or TLS fingerprint
- Blocking bad requests with attack signatures
- Applying global rate limiting
These three mitigations are applied incrementally to ensure that attackers are blocked as much as possible with no impact to legitimate users. However, the bulk of blocking activity frequently occurs in the initial combination of IP address and TLS fingerprint blocking or IP address‑only blocking phase. Fortunately, these are the exact rule types that can be effectively enforced by an eBPF program.
Rule Enforcement
NGINX App Protect DoS uses the created rules and applies them to incoming application traffic to block malicious requests. Since all application traffic is proxied to the backend (or upstream) application by the NGINX Plus proxy, any requests matching the blocking rules are simply dropped and not passed to the backend application.
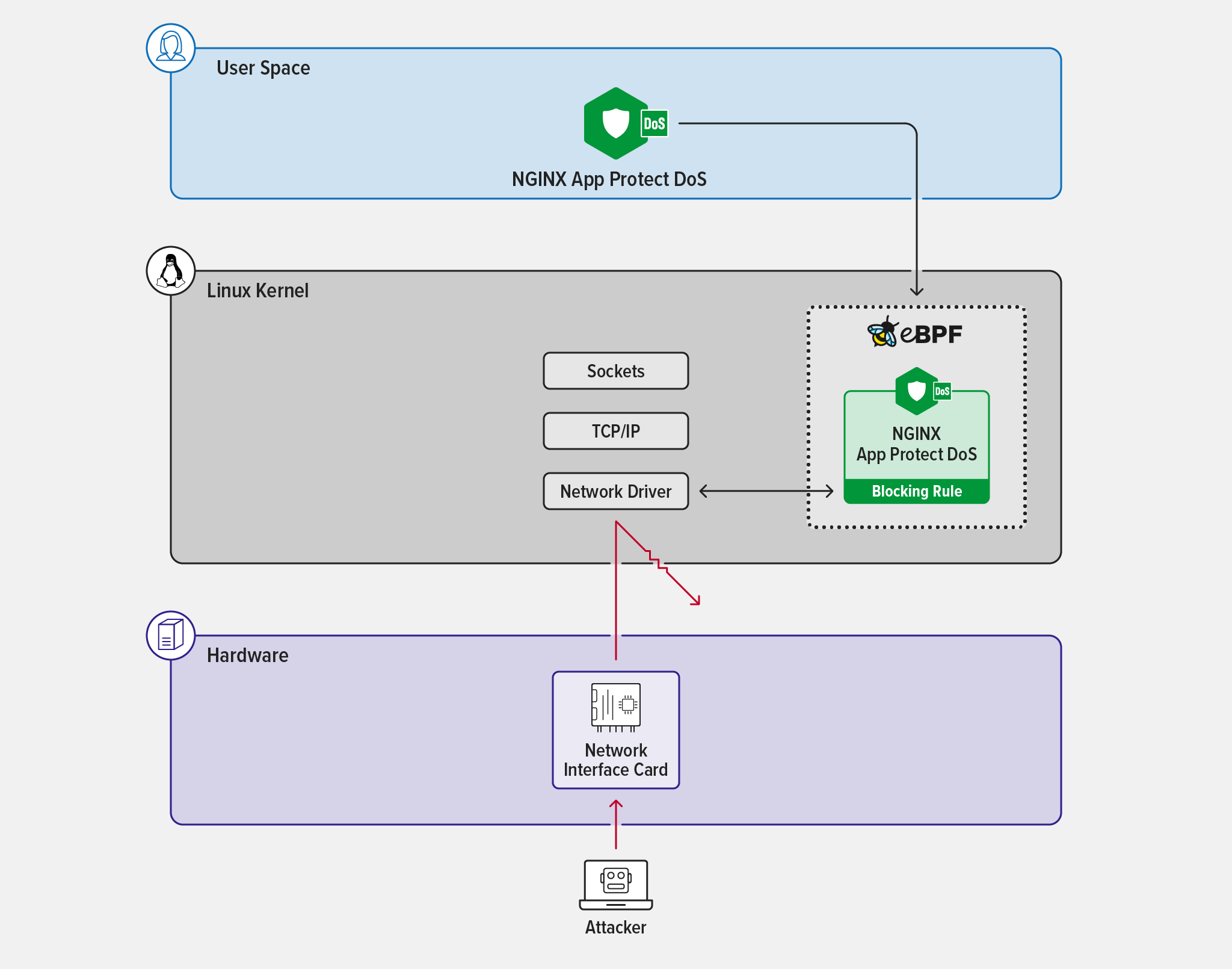
Even though NGINX Plus is a high‑performance proxy, it’s still possible for the additional workload created by the attack and mitigation rules to overwhelm the available resources of the platform NGINX is running on. This is where eBPF comes in. By applying IP address‑only blocking, or combining it with IP address and TLS fingerprint blocking in the kernel, malicious traffic can be assessed and blocked early at the transport layer (Layer 4). This has far greater efficiency than when performed by NGINX running in user space.
On supported platforms, when NGINX App Protect DoS creates rules to block attackers based on source IP address or TLS fingerprint, the rules are compiled into an eBPF bytecode program that is executed by the kernel when network events (known as hooks) occur. If a particular network event triggers the rule, the traffic is dropped early at Layer 4. This helps accelerate DDoS mitigation prior to reaching Layer 7. Since this activity all occurs in the kernel, it’s very efficient and can filter more traffic (before exhausting resources) than when the rules are implemented in user space.
Enabling eBPF Accelerated Mitigation on NGINX App Protect DoS
NGINX App Protect DoS accelerated mitigation is available on the following Linux Distributions:
- Alpine 3.15+
- Debian 11+
- RHEL 8+
- Ubuntu 20.04+
To enable accelerated DDoS mitigation, follow these steps:
- Install the eBPF‑enabled NGINX App Protect DoS package and perform any additional tasks. (See the installation documentation for details, as post‑installation tasks vary by distribution.)
- Configure NGINX App Protect DoS as usual.
-
Add the following directive in the
http{}block of the NGINX Plus configuration.protect_dos_accelerated_mitigation on; -
Reload the NGINX configuration.
$ sudo nginx -t && nginx -s reload
Summary
Combining the adaptive‑learning capabilities of NGINX App Protect DoS with the high‑efficiency traffic handling of eBPF kernel execution provides a multi‑layered, accelerated Layer 7 DDoS mitigation strategy with improved capabilities for today’s multi‑vector and application‑focused DDoS attacks. It additionally keeps infrastructure and compute costs down by decreasing the resources required to mitigate any given DDoS attack.
Test drive NGINX App Protect DoS for yourself with a 30-day free trial or contact us to discuss your use cases.
Additional Resources
- Whitepaper – Securing Modern Apps Against Layer 7 DoS Attacks
- Blog – How NGINX App Protect Denial of Service Adapts to the Evolving Attack Landscape
- Datasheet – Defend, Adapt and Mitigate Against Layer 7 DoS Attacks
The post Accelerating DDoS Mitigation with eBPF in F5 NGINX App Protect DoS appeared first on NGINX.
Source: Accelerating DDoS Mitigation with eBPF in F5 NGINX App Protect DoS






Leave a Reply