Defending Applications from Complex and Modern Attacks
Your friend Jon is shopping on his favorite e‑commerce site. One day, the site is slow and unresponsive. Over the next week, each time Jon wants to search for a product, the site remains sluggish. He wonders, “Does this site want my money or not?” Eventually, he decides to stop using the site because it’s become unreliable, and goes to a competitor to make his purchase.
Jon is an unusually patient shopper. Research reveals that a full third of U.S. consumers say they will abandon a brand after a single negative experience, and the percentage is even higher is other parts of the world.
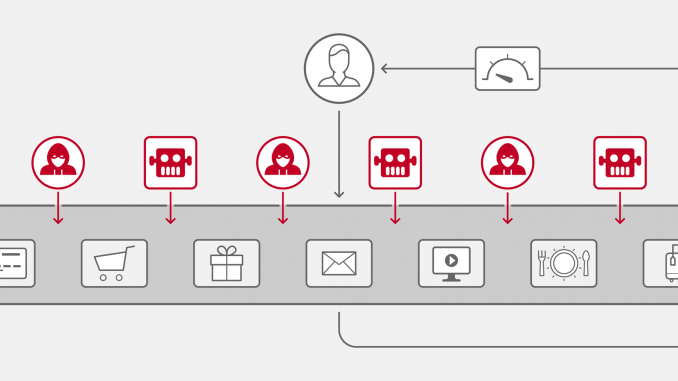
Beneath the surface, a likely cause for Jon’s poor user experience is a denial-of-service (DoS) attack. In a DoS attack, a bad actor bombards a site or application with requests, with the goal of overwhelming its servers to such an extent that they can send responses only very slowly or not at all. This effectively renders the site inaccessible.
The earliest DoS attacks flooded servers with requests for TCP or UDP connections (so‑called volumetric attacks) at the network and transport layers (Layers 3 and 4). Increasingly, though, DoS attacks use HTTP/HTTPS requests or API calls to attack at the application layer (Layer 7).
Bad actors can also launch distributed denial-of-service (DDoS) attacks by yoking together many computers into a botnet that sends requests. With DDoS attacks, not only is the possible number of requests greater, but the distributed nature of the attack makes it that much more difficult to figure out the source of the requests and block them.
Obviously, DoS attacks negatively affect user experience. And such attacks are on the rise:
- DoS attacks are among the most popular in part because of the proliferation of APIs
- Layer 7 attacks have increased by 20% in recent years, and the scale and severity of their impact has risen by nearly 200%
- The digital shift prompted by COVID‑19 was accompanied by a surge in DDoS attacks in 2020
Layer 7 attacks abuse apps, APIs, and other application resources in ways that hurt the user experience and prevent you from collecting revenue. So, whether the attack on an e‑commerce site is coming from a competing business, hacker, or any other source, site availability has a material impact on business operations, and ultimately revenue. To ensure users are able to access the services they need without interruption, including checkout, proper DoS protection is vital.
In this blog we answer two related questions about Layer 7 attacks. What makes them different and more complex than older types of attacks? What tools are best at combating them?
A New Kind of Attack
As we mentioned above, Layer 7 cyberattacks have evolved in response to the increasing complexity of the Internet and sophistication of application architectures. Volumetric attacks at Layers 3 and 4 – for example UDP reflection, and ICMP and SYN flooding – are not as prevalent as they used to be. Why? Infrastructure engineers have had a number of years to build defense mechanisms, making such attacks more difficult and less likely to succeed. That makes them more expensive to attackers, in terms of both money and time, and so they’ve moved on.
Layer 7 attacks are more complex to design than network attacks, and many tools that can handle Layer 3/4 attacks are ineffective at protecting modern application architectures. Layer 7 DDoS attacks are more difficult to detect because bots and automation allow attackers to disguise themselves as legitimate traffic, especially when they’re using sophisticated security penetration tools. When a hacker can assemble a botnet – thousands of compromised machines under the hacker’s control – it’s easy to initiate attacks on a huge scale. With bad bot traffic stealthily hiding among legitimate customer traffic, Layer 7 attacks create a new challenge.
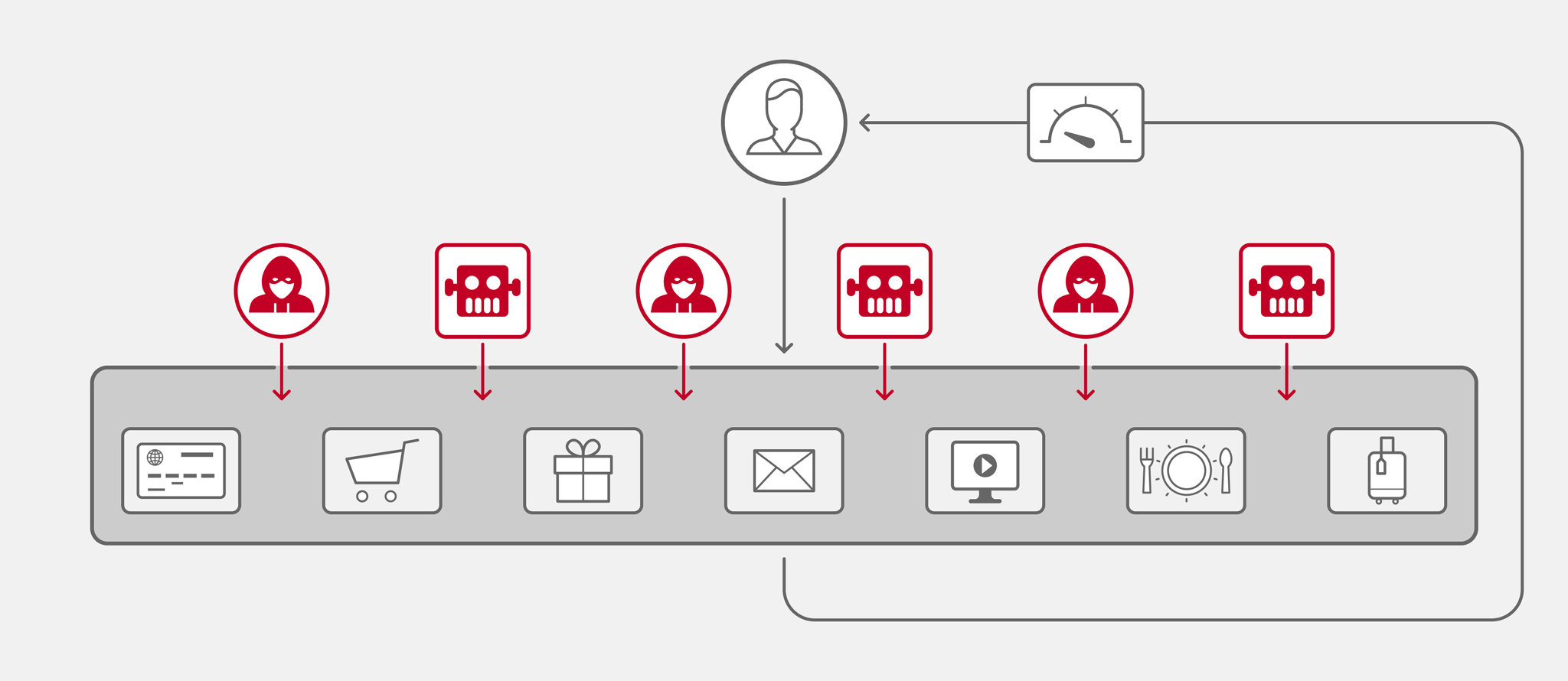
When the majority of attacks are made at the application layer, you need regular insight into application behavior to establish baselines that then help you determine whether or not traffic is malicious, ideally without burdening your valuable security team.
What’s Driving the Ballooning Growth in Layer 7 Attacks?
The world is not the same as it was when volumetric attacks were the norm. Today, devices and applications are developed at unprecedented speed. As environments shift into new landscapes, new vulnerabilities – and opportunities for attacks – arise.
For instance, devices used every day are fast becoming smart devices. According to Omdia, the total number of devices on the Internet of Things (IoT) reached 23.5 billion in 2020, and will likely reach 27.8 billion by the end of 2021. Unsurprisingly, the more devices there are, the more vulnerabilities are exposed. A big problem is that as phones, TVs, and refrigerators become connected IoT devices, security controls are often (and notoriously) overlooked. The lack of controls opens IoT devices to easy exploitation in botnets. With these new developments and 5G high capability on mobile devices, the landscape for DoS attacks and the potential impacts have grown significantly.
The exploitation of existing and new technologies at scale has become too easy for attackers. Modern landscapes and attacks on them require modern solutions. Otherwise, today’s smart devices and modern app architectures remain unguarded and open to attackers.
The High Cost of Layer 7 Attacks
With the world on lockdown during most of 2020 due to the COVID‑19 pandemic, consumers chose (or were forced) to buy even more products online, including everyday items they previously bought at the supermarket. Enterprises in turn had to accelerate their digital transformations to keep pace with demand. Unfortunately, cyber attackers exploited the increased reliance on the Internet, and DDoS attacks surged too.
As we saw with your friend Jon’s experience at the e‑commerce site, Layer 7 attacks can severely affect a site’s success. Imagine that poor performance being experienced by tens, hundreds, thousands, even millions of users. Without proper protection, a site can experience significant revenue loss, decreased customer satisfaction, increased customer churn, and even headlines and devastating damage to brand.
Worse yet, Layer 7 attacks are cheap to launch, but expensive to mitigate for the site owner. Without protection, recovery from an attack can take anywhere from days to weeks.
With the increasing scale and sophistication of DDoS attacks, only organizations with robust defenses can weather these battles. A true solution must protect a business against revenue‑impacting attacks that evade its traditional network and web defenses.
Finding a Modern Solution for a Modern Problem
So, what is the ideal solution? What are the key components that protect against Layer 7 attackers?
On a basic level, you need a tool that recognizes when your site is under attack – something that’s able to distinguish between “good guys” (legitimate traffic) and “bad guys” (malicious traffic). It must be able to do this not just in traditional environments with their more unified structure, but in modern, distributed app architectures employing microservices and Kubernetes. With the shift away from monolithic applications, tools designed to protect them are ineffective and a new approach must be used, one that is as adaptive and dynamic as the modern environments it protects.
What’s needed is DoS protection that works in both current and future landscapes. The salient aspect of modern landscapes is their ability to shift and change with ease. Today’s attackers are constantly changing their strategies, so attack‑prevention mechanisms must be able to observe changing user and service behavior and adapt continuously in response.

Today and in the future, teams need adaptable and powerful protection, focusing on safety, security, and speed:
- Seamless integration
Enabling strong security controls that integrate seamlessly into modern infrastructure architectures is key. Using a DoS solution with NGINX can minimize costs, reduce latency, accelerate performance, and improve user experience. Once integrated into the NGINX platform, our solution can reduce the complexity needed to safely deliver modern apps from code to customer across clouds and architectures. - High performance
A solution’s performance impact on customer experience and the application itself must be very minimal to nil, both under normal conditions and during an attack. Even while attacks are being actively averted, users can still access the application without any hindrance or adverse performance. Continuous monitoring and real‑time signatures with zero‑day attack protection ensure both optimum application performance and effective attack mitigation. - Agile security
To adapt at the breakneck pace of today’s digital world, a solution needs to be integrated into continuous integration and continuous development (CI/CD) pipelines, removing operational inefficiencies by automatically baselining and entering blocking mode once new code is deployed. In this adaptive solution, security can be automated to facilitate a “security as code” integration with DevOps tools. Protection happens automatically and prevents security from slowing down app innovation. - Attack prevention
Cyber attackers may adjust their tactics. To combat this, a dynamic solution is needed. With embedded tools for learning from user and service behavior, Layer 7 security is future‑proofed, and can react to attackers before any damage is incurred. Having unsupervised capability such as this allows for an automated feedback loop with multilayer defense – one with quick security remediations at the same speed as app evolution. Any behavior anomaly that is detected has a mitigation deployed automatically which is measured to ensure its effectiveness. - Reduced‑cost speed
Traditional security solutions can slow down DevOps workflows. CI/CD takes the deployment burden off developers so they can focus on delivering features, fast. It also gives emerging DevSecOps teams a way to integrate security into automated app delivery. With this streamlined workflow, no‑touch configuration enables cost‑effective protection at scale for distributed app and API environments like microservices, and removes friction between DevOps and SecOps teams.
For Layer 7 DoS protection, it’s essential to integrate flexible and adaptive products that can endure modern, ever‑changing landscapes. Business owners deserve the confidence that – with every digital shift – their site remains accessible, fast, and safe. And your friend Jon deserves a better shopping experience. If you don’t provide it, one of your competitors gladly will.
If you’d like to learn more about how to ensure proper protection, check out the NGINX App Protect – Denial of Service solution.
The post Defending Applications from Complex and Modern Attacks appeared first on NGINX.
Source: Defending Applications from Complex and Modern Attacks






Leave a Reply