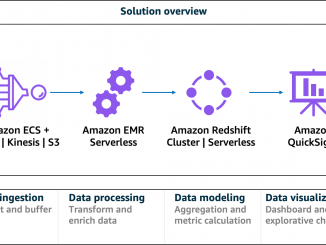
KCC 2023 후기 (2) 카카오 크루들과 함께
KCC 2023 후기 (2) 카카오 크루들과 함께 에릭이 앞서 소개해주신 것과 같이, 이번 6월 KCC 2023에 카카오 크루들이 함께 다녀왔습니다. 카카오가 올해도 KCC의 후원사로 참여했기 때문인데요, 이번 글에서는 저희가 직접 준비했던 후원사 학술세션을 소개해드리겠습니다. 수많은 후원사 로고 속에서 카카오 찾기 Kakao Tech Workshop KCC와 KSC에서 몇 차례 진행해오고 있는 Kakao Tech Workshop(이하 워크숍)을 소개합니다. 워크숍에서는 카카오의 추천 기술, 대용량 데이터 처리 기술, […] Source: KCC 2023 후기 (2) 카카오 크루들과 함께