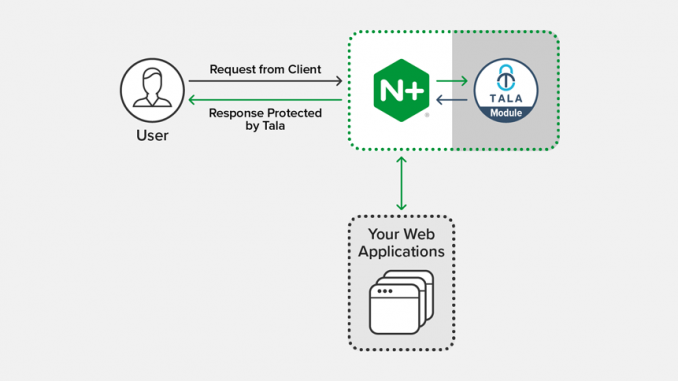
Redefining Client-Side Security with the Tala Security Certified Module for NGINX Plus
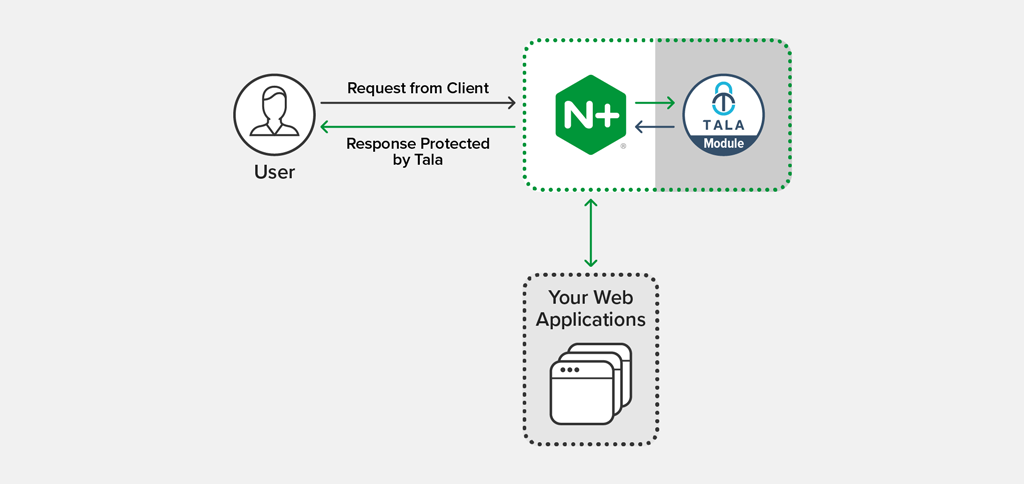
Up to 70% of the code rendering on websites today comes not from servers at the site, but via JavaScript integrations that operate outside the site’s security controls. This architecture enriches customer experience and engagement but also introduces critical vulnerabilities that enable client‑side attacks like Magecart. To understand how we can fix this problem, let’s start with a look at how we got here.
Fifteen years ago, when a user visited a website, all processing occurred on the server. The response sent to the client was mostly HTML code to be rendered, meaning the browser or client app was primarily a rendering engine.
Fast‑forward a few years and two key developments have transformed the architecture of modern web applications. First, companies like Google developed cloud‑based applications like GSuite to deliver the same user experience in the browser as traditional applications such as Microsoft Office provide on the desktop. Any changes made to a document were made locally, directly on the browser, instead of making round trips to the web server.
Second, the release of the iPhone and resulting growth in mobile devices drove a new requirement to support mobile applications over weak, intermittent, or high‑delay networks. These web apps must be able to work offline or in disconnected mode.
To make these new, innovative applications possible, developers turned to new technologies thahreft add power to the browser.
New Functionality, New Risk
The modern website architecture that supports cloud‑based applications and mobile devices relies on heavyweight frameworks – such as Angular, Backbone, Ember, and React – that leverage the processing power of the browser to execute code on the client side. When a user visits a website, the browser loads a significant volume of JavaScript, enabling the execution of code on the client side to provide an efficient, seamless end‑user experience. It is fair to say that the browser has, in many ways, become an operating system.
Visiting a website that leverages this modern architecture is comparable to the end‑user experience of the past, when the client had to download an executable before launching an application. Unfortunately, the security vulnerabilities introduced by this JavaScript‑reliant architecture have allowed attackers to compromise thousands of websites globally. These attacks, referred to by many names including Magecart, formjacking, and cross‑site scripting (XSS), mostly target online transactions and have had significant financial, regulatory, and reputational impacts.
With client‑side JavaScript running on 95% of all websites, confidence in e‑commerce is at stake.
Improving Website Security with the Tala Security Certified Module for NGINX Plus

Tala Security protects modern websites and web applications from critical and growing threats, such as XSS, Magecart, website supply‑chain attacks, clickjacking, and others. Our technology leverages more than 150 browser‑native controls to provide best-in-class, enterprise‑grade security for your web application, without the need for changes to application code, or for an agent or any JavaScript code on the client side.
Powered by an AI‑assisted analytics engine that evaluates more than 50 unique indicators to automate the generation, implementation, and updating of security, Tala Security’s product also provides customers with streamlined alert analytics and incident management.
Now we’re pleased to announce the availability of the Tala Security Certified Module for NGINX Plus.
Superfast Performance
NGINX and NGINX Plus are well known as a high‑performance web server, cache, and load balancer, powering more of the world’s websites than any other server. The Tala Security Certified Module leverages the core NGINX Plus engine to ensure no perceivable impact in performance for the end user – the module has a sub‑millisecond impact on the user response time.
NGINX Plus’s sophisticated event‑driven architecture can scale to hundreds of thousands of concurrent connections on modern hardware. The Tala Security Certified Module binds to this event‑driven architecture, enabling it to scale up and down seamlessly with NGINX Plus.
Simplified Administration
Tala Security’s real‑time protection installs within minutes on NGINX Plus and integrates easily with whatever NGINX Plus functionality you’re using (web server, reverse proxy, load balancer, cache), as well as all other NGINX modules.
Because the Tala Security Certified Module is loaded dynamically into the NGINX Plus runtime, it has a zero footprint on your application server. We call this a “touchless” security deployment, as neither your application codebase nor your application server has to be altered in any way. The Certified Module offers a frictionless user experience for those looking to integrate NGINX Plus with Tala Security.
Once installed, Tala Security’s low‑touch system continually monitors enterprise websites, third‑party services, and client‑side browser activity to ensure website security and integrity. With Tala Security, website security is assured and Infosec, risk and compliance, and development teams can utilize insightful reporting to investigate issues such as app vulnerabilities, compromised third parties, and low conversion rates.
Design
The Tala Security Certified Module has been architected on two core design principles: high availability and redundancy. It is designed with redundant components for continuous operation. We can ensure that Tala Security is not a single point of failure in your NGINX Plus infrastructure. The module follows a “fail‑open” paradigm in the worst‑case scenario, ensuring that your application is always running.
Over the past two years, we have performed rigorous testing in high‑load failover scenarios, incorporating fallback strategies to guarantee the caliber of the Tala Security Certified Module.
That is why we are proud that our module successfully met the stringent criteria for an NGINX Plus Certified Module.
Automation
We understand that managing hundreds of websites and subsidiaries in an enterprise is not an easy task, especially when you have to customize security policies for each section of each application without introducing any errors.
When it comes to security, one size does not fit all, but achieving best-in-class security that’s tailor‑made for your enterprise should not mean spending many months on integration and operational dependencies. With the Tala Security‑NGINX partnership, security automation truly comes alive, allowing you to focus on running your business.

Installing the Tala Security Certified Module
Installing the Tala Security Certified Module on your NGINX Plus server is a simple process that takes a matter of minutes. Before performing the installation, follow our instructions to do a Tala Security analysis of your web application.
Here is an example of installing the module on an NGINX Plus host.
-
Download the installation script onto the host:
$ curl -H 'auth-token: your_Tala_token' https://api.talasecurity.io/policy/installation/script -o tala_control.sh -
Install the module:
$ sudo bash tala_control.sh -v nginx -g -p 38
After a few minutes, the following message appears to indicate successful installation.
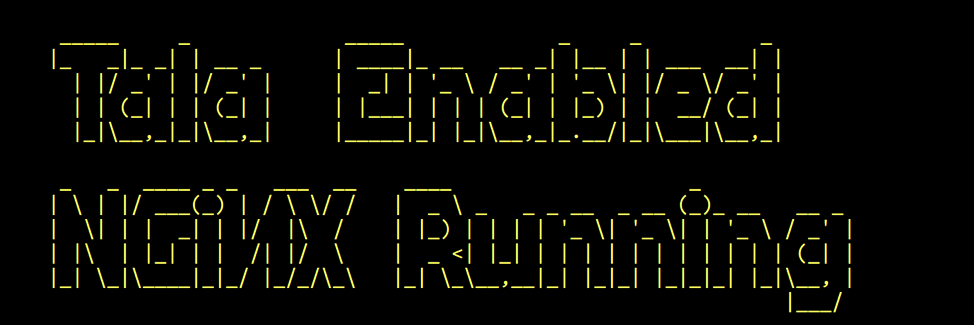
Conclusion
As a member of the NGINX Partner Network and F5 Partners, we at Tala Security look forward to working even more closely with the NGINX and F5 team. Tune in for future blogs and information around NGINX Plus and Tala Security!
About Tala Security
Tala Security secures millions of browser‑side web sessions for large providers in verticals such as financial services, online retail, payment processing, high‑tech, fintech, and education. Tala Security protects websites and web applications by continuously interrogating application architecture to enable the automation and continuous deployment of precise, browser‑native, standards‑based policies and controls. Our technology allows organizations to deploy standards‑based website security without the operational burdens associated with the generation and application of these policies.






Leave a Reply