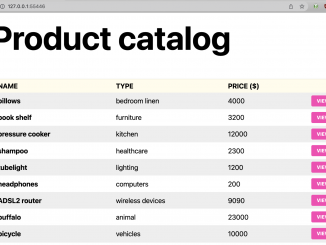
Advanced Kubernetes Deployment Strategies
Advanced Kubernetes Deployment Strategies This blog is the fifth in our five‑part series about Kubernetes networking for Microservices March 2022: Program overview: Microservices March 2022: Kubernetes Networking Unit 1: Architecting Kubernetes Clusters for High‑Traffic Websites Unit 2: Exposing APIs in Kubernetes Unit 3: Microservices Security Pattern in Kubernetes Unit 4: Advanced Kubernetes Deployment Strategies (this post) Once you get Kubernetes into production, you have to keep it there! In Unit 4, we address how Kubernetes networking can increase uptime and improve customer experiences. Three activities guide you progressively from a high‑level overview to practical application. We suggest you complete all three to get the best experience. Step 1: Watch the Livestream (1 Hour) Step 2: Deepen Your Knowledge (1–2 Hours) Step 3: Get Hands‑On (1 Hour) Step 1: Watch the Livestream (1 Hour) Each Microservices March livestream provides a high‑level overview of [ more… ]