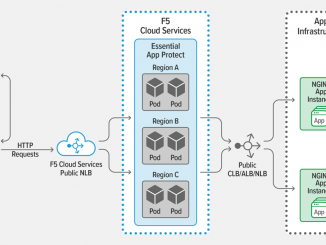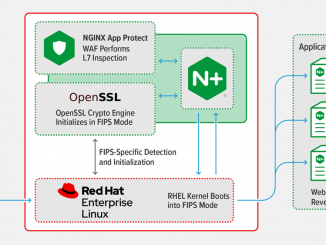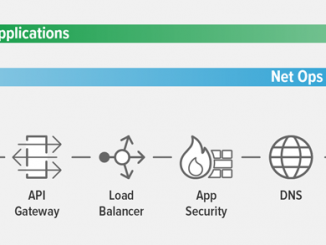
Deploying Application Services in Kubernetes, Part 1
Deploying Application Services in Kubernetes, Part 1 If we’ve observed just one change that has come with the growth of Kubernetes and cloud‑native architectures, it’s that DevOps teams and application owners are taking more direct control over how their applications are deployed, managed, and delivered. Modern applications benefit from an increasingly sophisticated set of supporting “application services” to ensure their successful operation in production. The separation between the application and its supporting services has become blurred, and DevOps engineers are discovering that they need to influence or own these services. Let’s look at a couple of specific examples: Canary and blue‑green deployments – DevOps teams are pushing applications into production, sometimes multiple times per day. They actively use the traffic‑steering capabilities of the load balancer or application delivery controller (ADC) to validate new application instances with small quantities of traffic before [ more… ]