Public Preview : Improve Win32 app security via app isolation
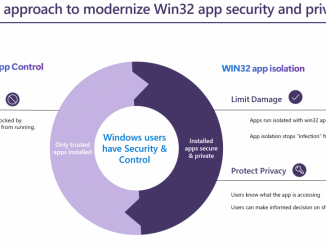
Public Preview : Improve Win32 app security via app isolation We are thrilled to announce the public preview launch of Win32 app isolation. This blog post provides an overview of the topic. To learn more about the developer experience and engage with the team, please visit our GitHub page. It is worth noting that Win32 app isolation is an addition to the family of existing Windows sandbox options, such as Windows Sandbox and Microsoft Defender Application Guard. While these options are based on virtualization based security, Win32 app isolation is built on the foundation of AppContainers (and more). AppContainers are specifically designed to encapsulate and restrict the execution of processes, helping to ensure they operate with limited privileges, commonly referred to as low integrity levels. Win32 App isolation The frequency and impact of zero-day vulnerabilities have witnessed a substantial increase [ more… ]

