The Imperva HTTP/2 Vulnerability Report and NGINX

On Thursday, August 4th, Imperva – an Internet security company – announced four potential security vulnerabilities in the HTTP/2 protocol, and issued a detailed report evaluating a number of webservers against these vulnerabilities.
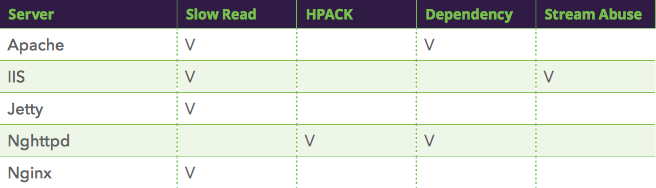
NGINX 1.9.9 performed comparatively well in Imperva’s tests, and was not affected by three of the four potential vulnerabilities. Attempts to exploit the remaining vulnerability, “Slow Read”, caused a resource leakage in NGINX and ultimately allowed a denial-of-service attack against HTTP/2 services.

The fault was reported to NGINX, and was resolved promptly in the NGINX 1.9.12 and NGINX Plus R9 releases. We are pleased to confirm that none of the current versions of NGINX – NGINX Plus, NGINX ‘mainline’, NGINX ‘stable’ – are vulnerable to any of the potential attacks described by Imperva.
If you are using an older version of NGINX with HTTP/2, you should update your NGINX software. HTTP/2 is a complex and relatively new protocol, so it is wise to run the latest software versions at all times.
You should also review the NGINX tuning best practices. A default Linux configuration is often quite conservative in its tuning, and you should consider increasing some of the tuning parameters to increase the capacity of your NGINX system.
The Problem
As of August 2016, HTTP/2 is currently in use on roughly 9% of all websites, including very popular sites such as FaceBook, Google, and Wikipedia. Content delivery network (CDN) providers that use NGINX and NGINX Plus often include HTTP/2 as part of their offerings.
The complex design of HTTP/2 means there are many possible avenues that researchers can explore to seek out design or implementation weaknesses. The Imperva reports describes four potential vulnerabilities in HTTP/2.
When Imperva tested various web servers to see if they exhibited vulnerabilities, a variation of their “Slow Read” test exposed a resource-leakage bug in NGINX and NGINX Plus. This resource leakage ultimately resulted in a denial of service.
NGINX is not generally vulnerable to “Slow Read” attacks (often known as
Slowloris). Imperva’s test case helped us to isolate this previously-reported resource leakage bug. We were then able to address this error case by adding additional timeouts and guards to ensure that HTTP/2 resources were closed and released correctly, and we were able to verify that these measures are effective.
Mitigation
If you are using an older version of NGINX and have implemented HTTP/2, we strongly recommend upgrading to NGINX 1.9.12 or NGINX Plus R9, or later. These releases of NGINX do not exhibit the resource leakage bug that was exposed by Imperva’s test case.
NGINX and NGINX Plus provide effective ways to defeat the relevant vulnerability described in the Imperva report, and upgrading to the latest release of either product eliminates the vulnerability entirely.
We also recommend that you consider the steps described in our post on mitigating DDoS attacks; recommended steps include:
- Limiting the rate of requests from any single user using
limit_req - Limiting the number of connections that can be opened by a single client using
limit_conn - Closing connections more quickly with more aggressive timeouts
If you have any questions, please comment on this post – or, if you are an NGINX Plus subscriber, don’t hesitate to contact our support team for assistance.
The post The Imperva HTTP/2 Vulnerability Report and NGINX appeared first on NGINX.




Leave a Reply